A Windows security update delivered in January and presently completely authorized for the current month is making Windows clients experience 0x0000011b mistakes when printing to arrange printers.
In January 2021, Microsoft delivered a security update to fix a ‘Windows Print Spooler Spoofing Vulnerability’ followed as CVE-2021-1678.
“A security sidestep weakness exists in the manner the Printer Remote Procedure Call (RPC) restricting handles confirmation for the far off Winspool interface,” clarifies a help notice about the weakness.
At the point when the security update was delivered, it didn’t naturally shield gadgets from the weakness. In any case, it added another Registry key that administrators could use to build the RPC confirmation level utilized for network printing to relieve the weakness.
At the end of the day, this security update didn’t fix any weakness except if a Windows overseer made the accompanying Registry key:
[HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Print]
“RpcAuthnLevelPrivacyEnabled”=dword:00000001
Nonetheless, in the current month’s September fourteenth Patch Tuesday security refreshes, Microsoft naturally empowered this setting as a matter of course for each window gadget regardless of whether that Registry setting was not made.
When this alleviation was empowered naturally, Windows clients started encountering 0x0000011b mistakes when printing to organize printers.
This printing blunder is mostly found in private venture and home organizations that can’t exploit a Kerberos arrangement on a Windows space.
Uninstalling September’s Windows security updates will fix the issue, yet presently the gadgets will be helpless against two weaknesses, PrintNightmare and MSHTML, effectively took advantage of by danger entertainers.
A superior strategy is to handicap the relief for CVE-2021-1678 until Microsoft comes out with new direction, as that weakness isn’t effectively taken advantage of.
How to fix the 0x0000011b printing errors
To fix the recent 0x0000011b printing errors without removing the current Windows Updates (KB5005565), you can instead disable the CVE-2021-1678 mitigation enabled by default this month.
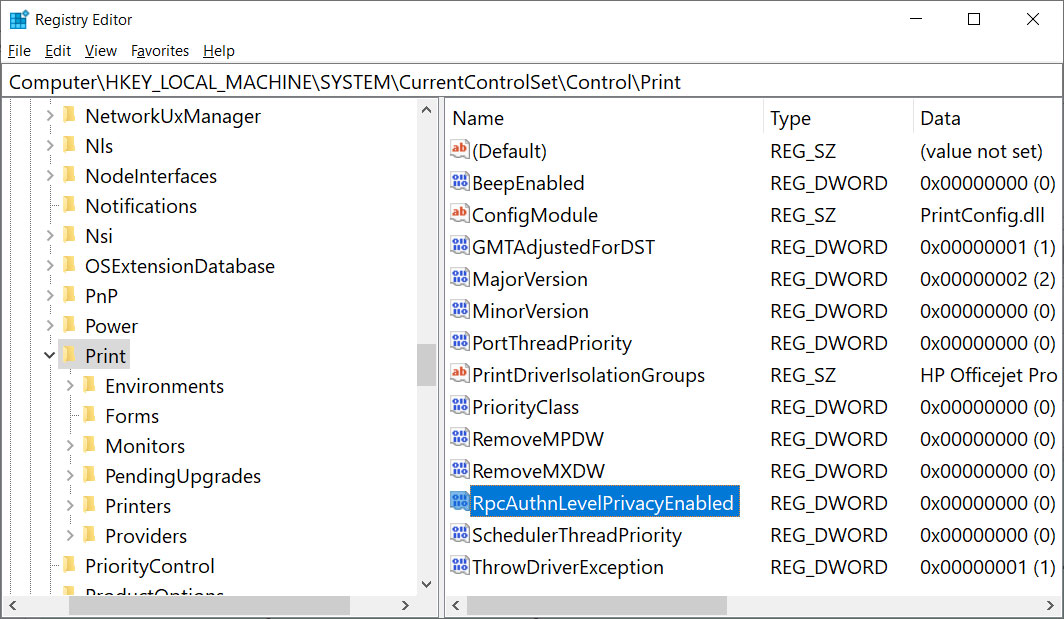
To do that, open the Windows Registry Editor and navigate to the HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Print key, create a new DWORD-32 bit value named RpcAuthnLevelPrivacyEnabled, and set it to 0, as shown in the Registry file below.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Print]
“RpcAuthnLevelPrivacyEnabled”=dword:00000000
To make it easier to add this change, you can use the fix-0x0000011b.reg Registry file to add it for you.
Download this file on both your print server and your Windows devices connecting to it, double-click on it, and allow the data to be merged.
Once you disable this mitigation, you will no longer be protected from the vulnerability, but it will hopefully allow you to print again.
If this does not solve your problem, use the enable-RpcAuthnLevel.reg to go back to the Windows defaults.
